Security Concepts
Cyber threats and risks
Cybersecurity refers to the technologies, processes, and practices designed to protect an organization's intellectual property, customer data, and other sensitive information from unauthorized access by cybercriminals.
The frequency and severity of cybercrime are on the rise and there is a significant need for improved cybersecurity risk management as part of every organization's enterprise risk profile. It's one of the top risks to any business.
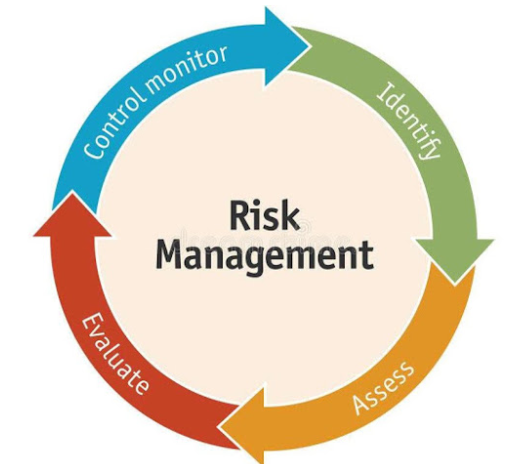
The threat lifecycle is important for risk assessment because it shows where you can mitigate threats. The goal is to reduce the number of vulnerabilities and to address them as early as possible. For example, discouraging an attacker who is probing a system for vulnerabilities can eliminate a threat.
The risk and threat assessment process includes the following steps:
Identify information and security risks
Assess and prioritize risks
Implement policy, procedures, and technical solutions to mitigate these risks
The overall process of risk and threat assessment, and the implementation of security controls, is referred to as a risk management framework. This document refers to NIST security and privacy controls and other publications about risk management frameworks.
Importance of NIST standards
The NIST CSF provides organizations with cybersecurity best practices that can help them identify, assess and prioritize their cyber risks. The framework also helps to improve communication between different organization departments by providing an integrated approach to cybersecurity planning across all areas of an organization.
Hardening
Developing and implementing security measures and best practices are known as "hardening."
Hardening is a continuous process of identifying and understanding security risks and taking appropriate steps to counter them. The process is dynamic because threats, and the systems they target, are continuously evolving.
Hardening establishes actions that mitigate threats for each phase in the threat lifecycle. For example, during the reconnaissance phase, an attacker scans to find open ports and determine the status of services that are related to the network and the VMS. To mitigate this, the hardening guidance is to close unnecessary system ports in Mirasys VMS and Windows configurations.
While most of the information in this guide focuses on IT settings and techniques, it is important to remember that physical security is also a vital part of hardening. For example, use physical barriers to servers and client computers, and make sure that things like camera enclosures, locks, tamper alarms, and access controls are secure.
The following are the actionable steps for hardening a VMS
Understand the components to protect
Harden the surveillance system components:
Document and maintain security settings on each system
Train and invest in people and skills, including your supply chain
Cybersecurity Framework
The Framework is voluntary guidance, based on existing standards, guidelines, and practices for organizations to better manage and reduce cybersecurity risk. In addition to helping organizations manage and reduce risks, it was designed to foster risk and cybersecurity management communications amongst both internal and external organizational stakeholders.
The Cybersecurity Framework consists of three main components: the Core, Implementation Tiers, and Profiles.
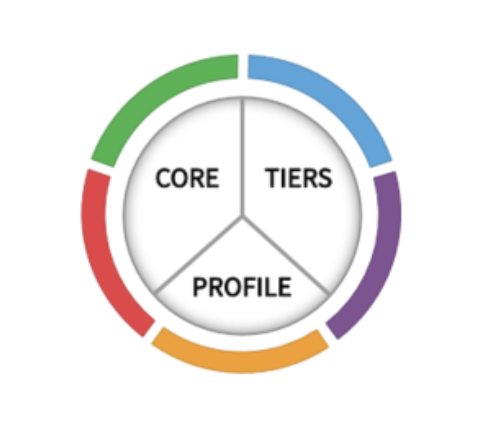
Framework Core
The Core is a set of desired cybersecurity activities and outcomes organized into Categories and aligned to Informative References. The Framework Core is designed to be intuitive and to act as a translation layer to enable communication between multi-disciplinary teams by using simplistic and non-technical language.
The Core consists of three parts:
Functions
Categories
Subcategories.
The Core includes five high-level functions:
Identify
Protect
Detect
Respond
Recover
These 5 functions are not only applicable to cybersecurity risk management but also to risk management at large. The next level down is the 23 Categories that are split across the five Functions. The image below depicts the Framework Core's Functions and Categories.
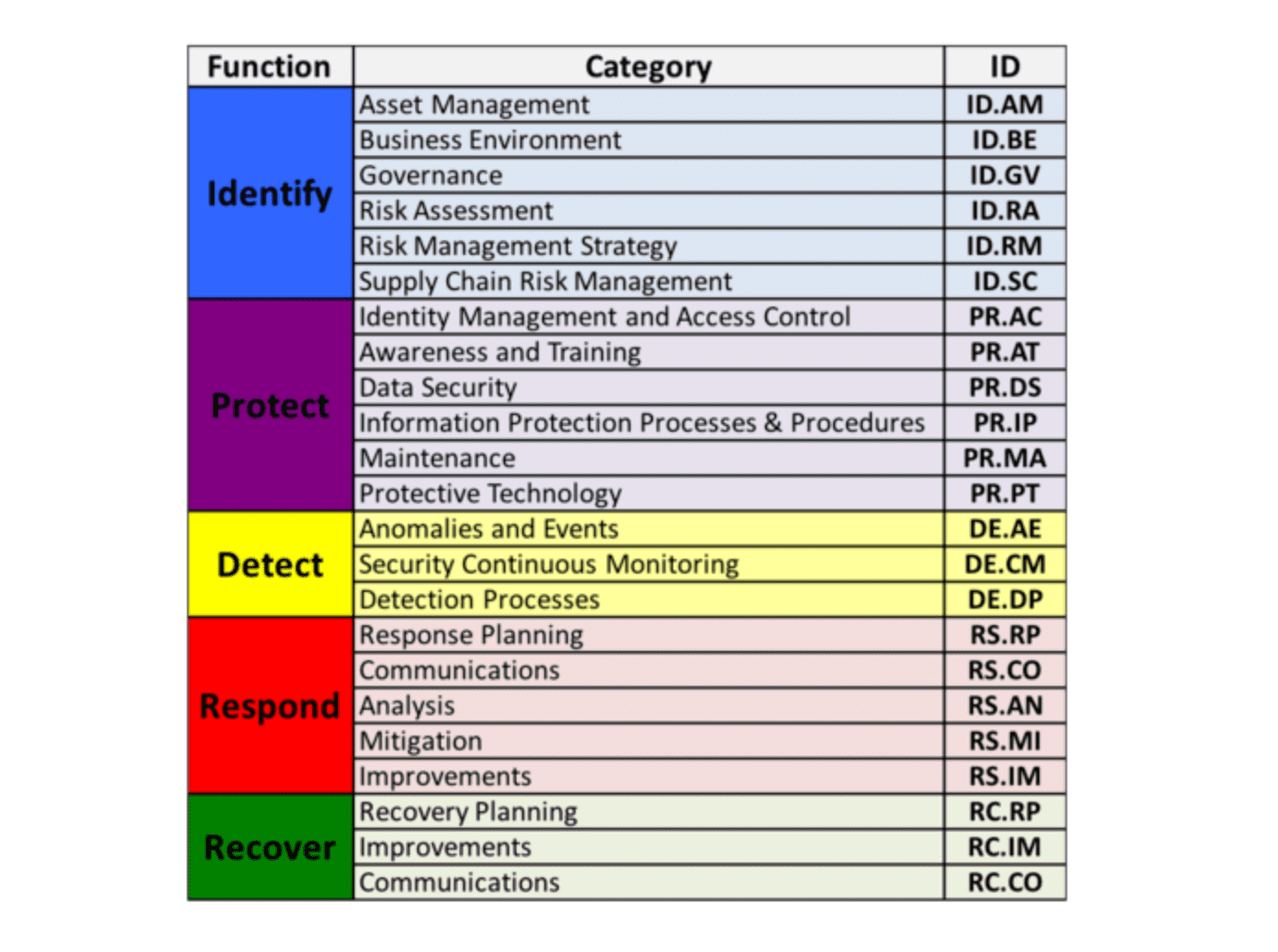
The Categories were designed to cover the breadth of cybersecurity objectives for an organization, while not being overly detailed. It covers topics across cyber, physical, and personnel, with a focus on business outcomes.
Framework Implementation Tiers
Tiers describe the degree to which an organization’s cybersecurity risk management practices exhibit the characteristics defined in the Framework.
The Tiers range from Partial (Tier 1) to Adaptive (Tier 4) and describe an increasing degree of rigor, how well-integrated cybersecurity risk decisions are into broader risk decisions, and the degree to which the organization shares and receives cybersecurity info from external parties.
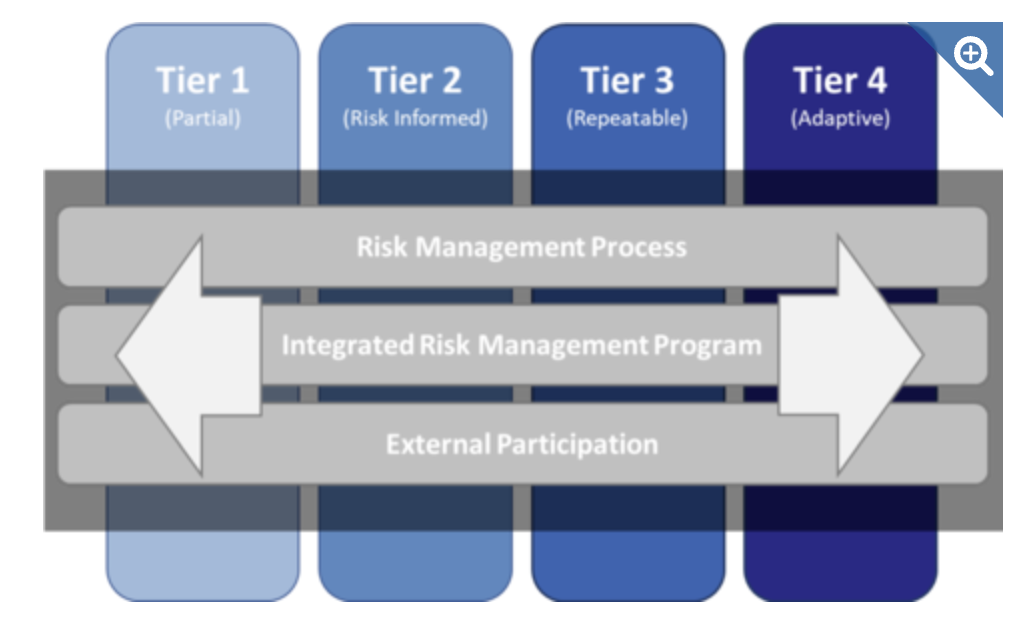
Tiers do not necessarily represent maturity levels. Organizations should determine the desired Tier, ensuring that the selected level meets organizational goals, reduces cybersecurity risk to levels acceptable to the organization, and is feasible to implement, fiscally and otherwise.
Framework Profiles
Profiles are an organization's unique alignment of its organizational requirements and objectives, risk appetite, and resources against the desired outcomes of the Framework Core.
Profiles can be used to identify opportunities for improving cybersecurity posture by comparing a “Current” Profile with a “Target” Profile.
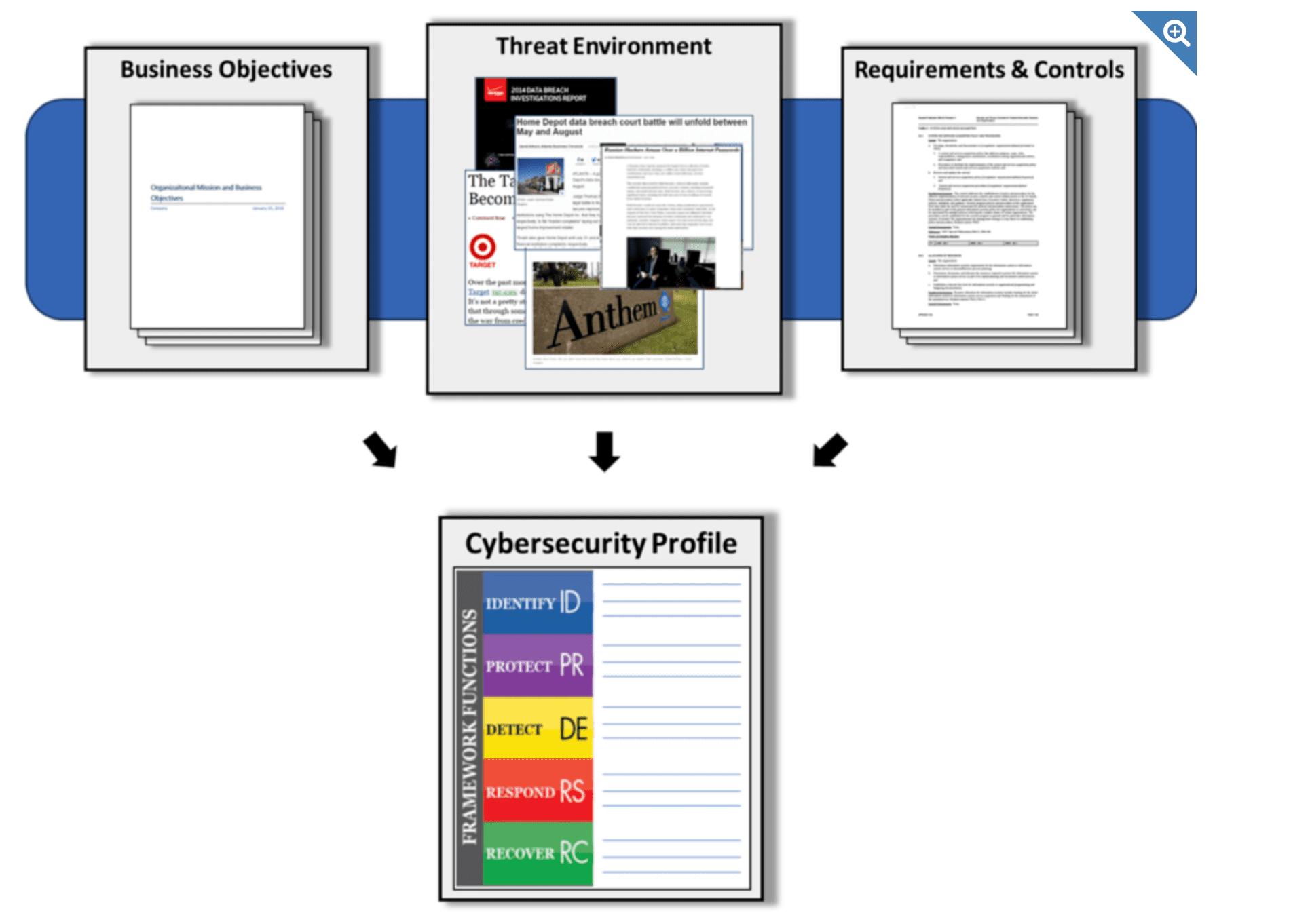
Profiles are about optimizing the Cybersecurity Framework to best serve the organization. The Framework is voluntary, so there is no ‘right’ or ‘wrong’ way to do it. One way of approaching profiles is for an organization to map its cybersecurity requirements, mission objectives, and operating methodologies, along with current practices against the subcategories of the Framework Core to create a Current-State Profile. These requirements and objectives can be compared against the current operating state of the organization to gain an understanding of the gaps between the two.
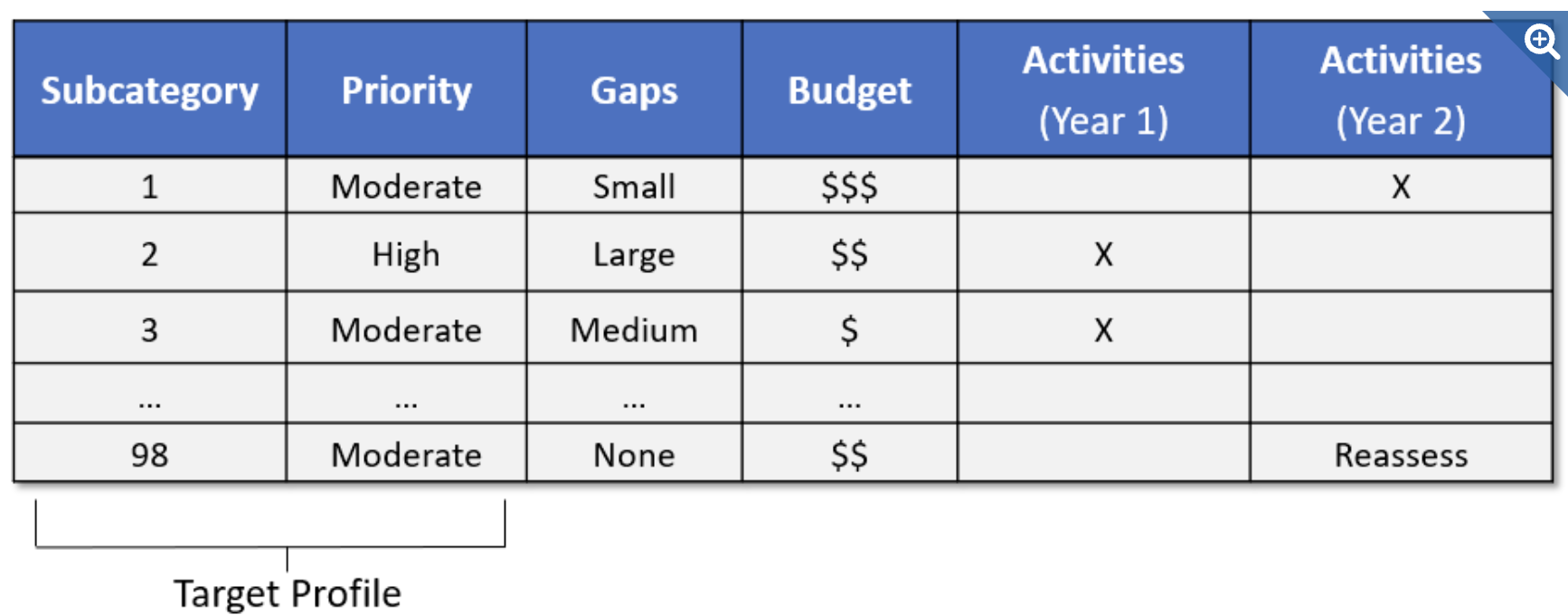
The creation of these profiles and the gap analysis allows organizations to create a prioritized implementation plan. The priority, size of the gap, and estimated cost of the corrective actions help organizations plan and budget for cybersecurity improvement activities.
